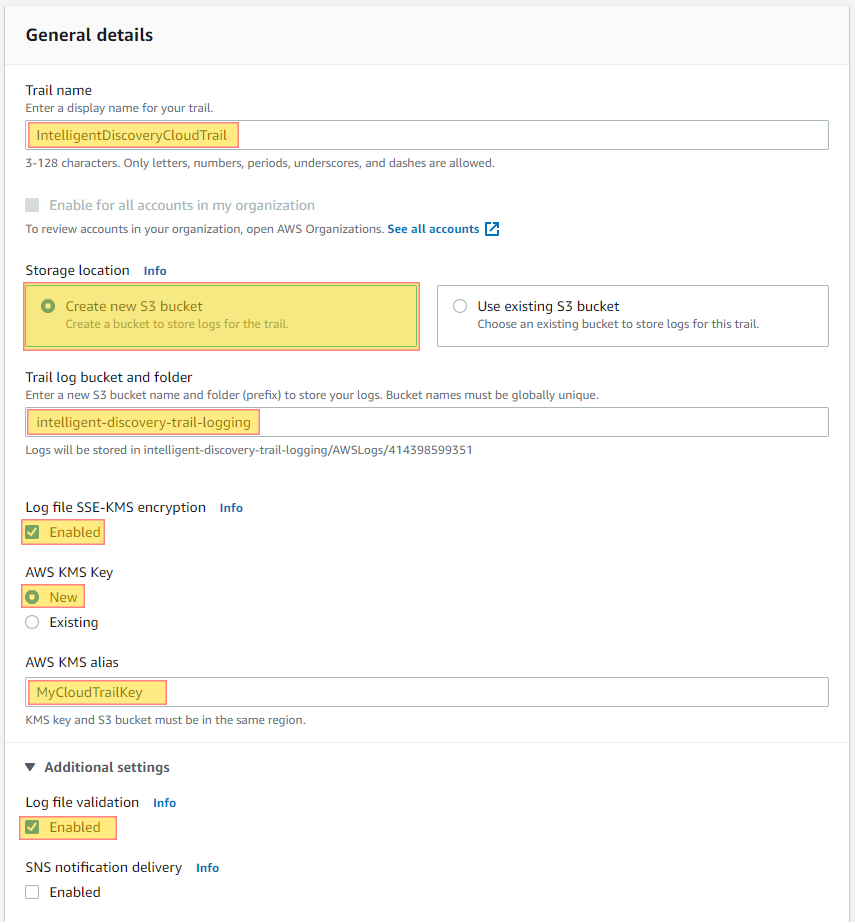
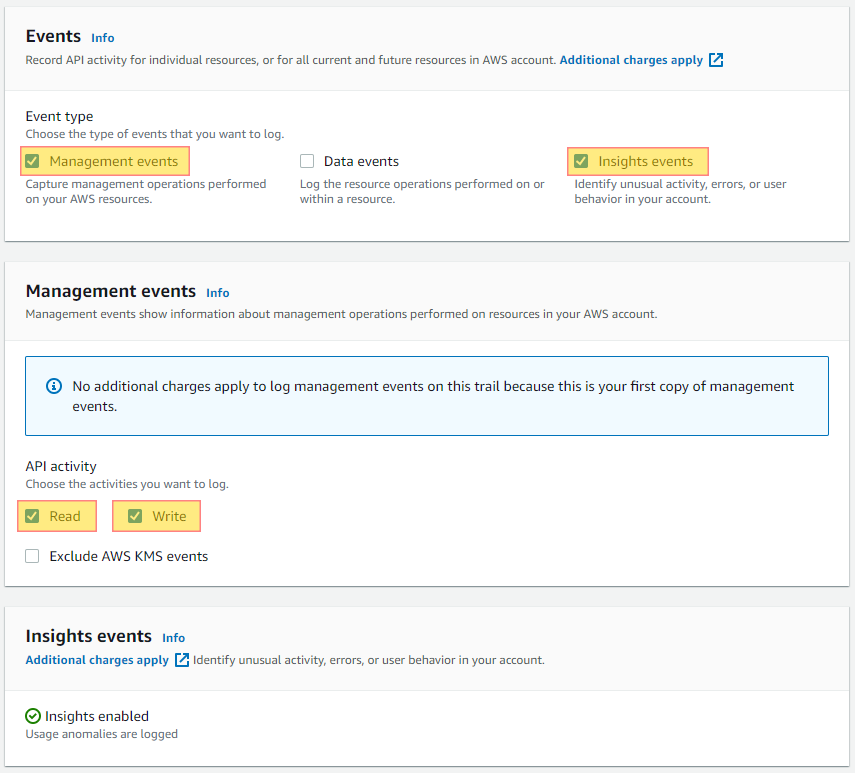
AWS CloudTrail is a service that enables governance, compliance, operational auditing, and risk auditing of your AWS account. With CloudTrail, you can log, continuously monitor, and retain account activity related to actions across your AWS infrastructure. CloudTrail provides event history of your AWS account activity, including actions taken through the AWS Management Console, AWS SDKs, command line tools, and other AWS services. This is why CloudTrail is a security best practice. Having a full inventory of your CloudTrails with current logging status across all of your accounts can help with CIS, NIST, HIPPA, GDPR & PCI-DSS compliance.
Do you want to see all of your ACM certificates in once place for all regions and all accounts?
Login to our online demo to see exactly what this looks like.
demo.intelligentdiscovery.io
Consolidate your inventory management with consistent and frequent security logs, inventories, and change logs. Dashboard reporting for extensive analytical value.
learn more +Access consolidated capacity, cost, and volume tools in a scaling environment without impacting production or breaking the bank.
learn more +