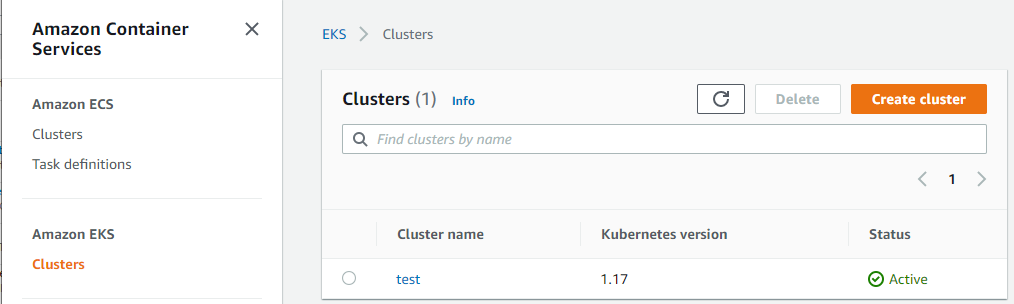
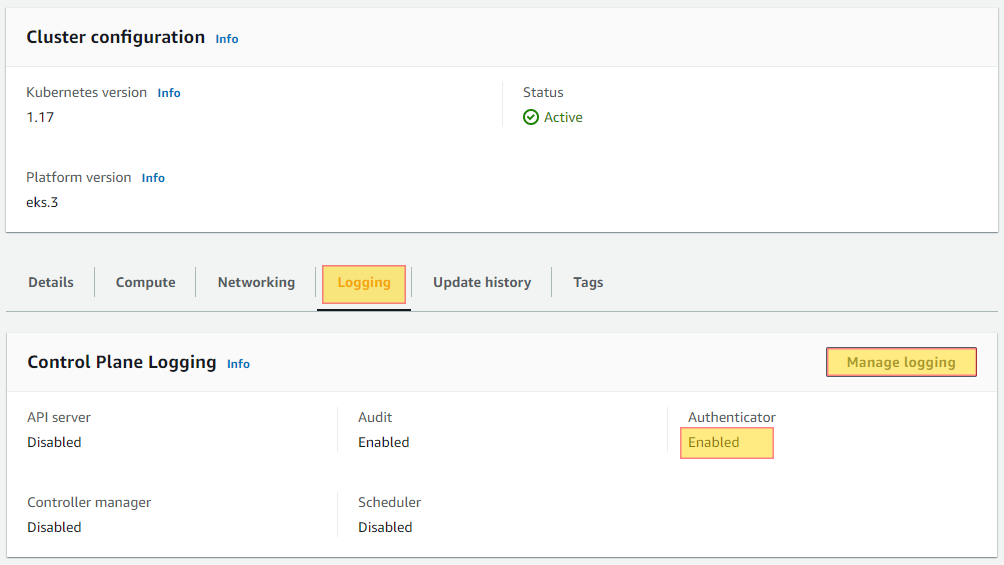
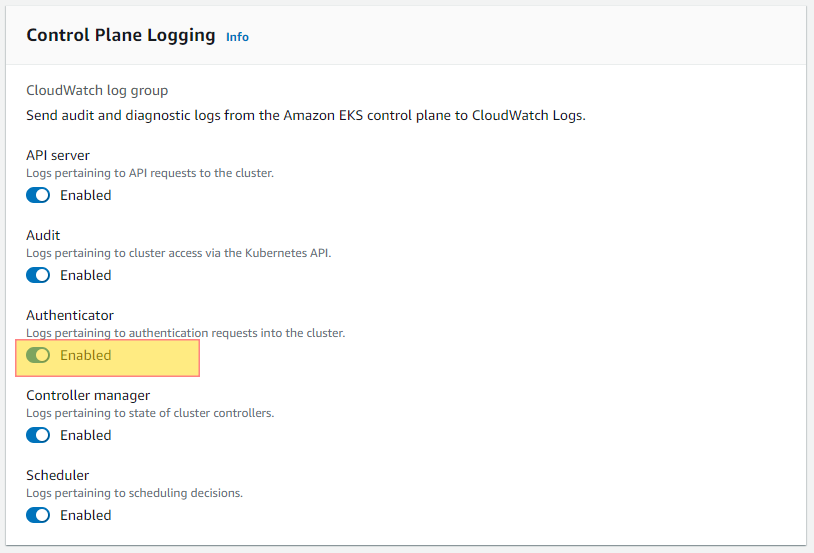
Authenticator logging is crucial to have enabled in order have full insight into who has interacted or made changes with the Kubernetes cluster via the api. For this reason having audit logging enabled is considered a security best practice to and should be enabled. Ensuring this is enabled will help you with PCI-DSS, HIPPA and GDPR compliance.
Do you want to see all of your AWS EC2 Instances in once place for all regions and all accounts?
Login to our online demo to see exactly what this looks like.
demo.intelligentdiscovery.io
Consolidate your inventory management with consistent and frequent security logs, inventories, and change logs. Dashboard reporting for extensive analytical value.
learn more +Access consolidated capacity, cost, and volume tools in a scaling environment without impacting production or breaking the bank.
learn more +